By Todd Cramer, Intel, Director Security Ecosystem, and Ram Chary, Intel, Senior Director of Platform Security
In his blog post, “What is an AI PC and How Can It Help Me?” Robert Hallock elegantly defined an AI PC as a new computer with components that are specifically designed to run powerful AI-accelerated software.
These amazing PCs are transforming business. Anyone who creates things on an AI PC can now accomplish more in less time. Drafting a report or editing an image? The time it takes employees to generate content has dropped dramatically with AI, spawning a revolution in business productivity.
But AI PCs offer more than massive productivity increases. Built with the Intel® Core™ Ultra processors, the AI capabilities of these PCs can also be applied to enhance security. AI for security, for example, can autonomously classify malware, make sense of anomalies in code, categorize threats, execute attack simulations, and summarize vulnerability reports faster than any human to name a few innovations.
AI for security is important because malicious actors are using new techniques that are skilled at evading traditional defenses: 75 percent of attacks are now fileless, meaning bad actors inject malicious code directly into computer memory, where it is hard to distinguish from valid system processes.2 AI holds unique potential to quickly correlate and discover never-before-seen attacks and systemanomalous behavior . This blog post discusses how AI PCs can help protect businesses using AI for security. In this blog we’ll share how technologies like Intel® Threat Detection Technology (Intel® TDT) and the neural processing units (NPUs) available in Intel Core Ultra processors enhance security at the silicon level.
A history of AI for security innovations
Six years ago, Intel researchers started exploring the potential of fingerprinting malware by applying machine learning (ML) algorithms to telemetry data derived from malware executing on the CPU microarchitecture. Intel shared an early proof of concept (POC) of this technology at an RSA conference in 2020.
In 2018, Intel productized this technology as Intel TDT. Intel TDT can identify targeted attacks such as cryptojacking and ransomware using silicon-level telemetry and AI. Beyond targeted attacks, in 2022 Intel and Microsoft delivered research that showed CPU telemetry is useful to model the good behavior of system application processes and use this as a baseline to identify software supply chain attacks. Fast forward to today, and Intel has scaled its AI for security innovations with its security ecosystem to improve protections on more than one billion PCs!
Figure 1. Intel has evolved Intel TDT to support security innovations
Intel TDT delivers AI at scale today
Intel TDT is a software development kit (SDK) at its heart. Security ISVs use the SDK to integrate AI-based threat detection into endpoint detection and response (EDR) solutions that run on Intel Core processor–based PCs from the 9th Generation onwards.
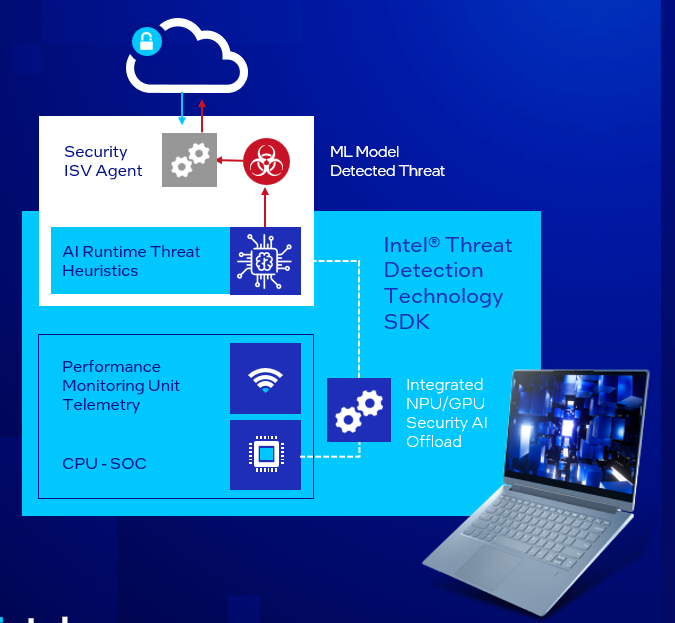
Figure 2 shows how Intel TDT uses telemetry from dense performance monitoring unit (PMU) telemetry that tracks fine-grained application processes running on the CPU microarchitecture. As malware executes in the operating system (OS) and on the software layers above, it leaves a fingerprint on the CPU’s PMU that can be modeled in AI to identify specific indicators of attack. The AI component of Intel TDT is comprised of random-forest-classifier-based ML that is itself suited for offload on the Intel integrated GPU. AI for security stays in the background to keep the user’s compute experience intact.
Figure 2. Intel TDT applies ML to low-level hardware telemetry
Because malware deploys obfuscation and cloaking techniques, traditional file-based threat detection techniques can miss it many of the attacks that Intel TDT can detect. However, when ISVs integrate Intel TDT into their antivirus and EDR solutions, they can detect malware earlier.
By pairing AI PCs with EDR software from Microsoft, Acronix, Bytesatwork, CrowdStrike, Check Point, Trend Micro, Sequretek, Fidelis, Kingsoft, and ESET, IT fleet managers can step up defenses using the PC hardware itself to aid in detections.
From an efficacy standpoint, SE Labs’ recent tests showed that Intel TDT detected 93 percent of the top ransomware attacks. These results are so significant that security industry analysts now factor in Intel TDT enablement when ranking ISVs’ security solutions.
New AI-powered detection at the endpoint
The NPU available within new Intel Core Ultra processors is another foundation of AI-powered threat detection on AI PCs. The Intel NPU is a dedicated low-power AI engine that can run deep learning (DL) models on the processor. DL is a subset of ML that uses artificial neural networks to learn from data and make predictions. These neural networks are composed of layers of interconnected nodes that mimic the human brain's structure, allowing them to excel at tasks involving pattern recognition, image processing, natural language processing, and more.
By using the Intel NPU, EDR ISVs can move AI-based threat detection from the cloud to the AI PC endpoint. This provides a long list of benefits, including:
- Reduced latency and real-time threat detection: When DL models run on the endpoint, data processing occurs locally, reducing the need for round-trip communication to the cloud. Real-time decisions can be made without waiting for cloud-based processing, which can be crucial for real-time threat detection.
- Processing data locally preserves network bandwidth: Transmitting large volumes of data to the cloud can strain network bandwidth. By processing data locally, only relevant insights or anomalies need to be sent to the cloud, minimizing data transfer. This increases the volume of data that can be processed at the endpoint, enhancing threat detection.
- Enhanced privacy: Endpoint-based DL allows organizations to maintain control over their data, especially when dealing with personally identifiable information (PII) or confidential business data. View the Bufferzone PR on new anti-phishing solutions that ensure user privacy.
- Innovative new security approaches: Unleashing DL on the edge opens the door for new types of threat detection. Solution providers can creatively and dynamically discover malware in real time locally, leading to faster remediation. View the CrowdStrike blog and video on the potential AI on the endpoint.
The right choice for new fleet purchases
AI PCs can help businesses drive productivity through the roof. But they can do more than that. They offer robust AI enhancement, enabling security capabilities to help businesses progress against ever-evolving ransomware threats. With Intel TDT and Intel Core Ultra processors featuring the Intel NPU, AI PCs take hardware-based security to a new level. When productivity and security are priorities, AI PCs are the right choice for new fleet purchases.
Learn more about AI PCs by visiting intel.com/aipc.
Learn more about Intel hardware-enabled security.
___________________________________________________________________________________________
Sources & Legal Disclaimers
1 Intel. “On-demand webinar: How AI unlocks new strategies to fight ransomware.” December 2023. https://webinar.intel.com/ai-to-fight-ransomware-ondemand-conf.
2 PC Magazine. “Ransomware Attacks Rake in Over $1 Billion in 2023 for New Record.” February 2024. pcmag.com/news/ransomware-attacks-rake-in-over-1-billion-in-2023-for-new-record.
Intel technologies may require enabled hardware, software or service activation.
No product or component can be absolutely secure.
Your costs and results may vary.
©Intel Corporation. Intel, the Intel logo, other Intel marks are trademarks of Intel Corporation or its subsidiaries. Other names and brands may be claimed as the property of others.
 I am a versatile technology leader with a 25+ year track record of creating customer value and delivering business growth through a combination of innovation and diligent execution. My success is based on a combination of deep technical expertise, business acumen, as well as hands-on experience across advanced research, product development, product management, and ecosystem building.
I am passionate about building high achieving, cross-functional world-wide teams that create sustainable business opportunities through the application of disruptive technologies that are broadly deployed on 100s of millions of systems.
My deep technical experience & expertise starts with the creative application of Artificial Intelligence to solve cybersecurity issues, built on a deep understanding of the underlying Operating systems & Hardware environments.
I enjoy engaging audiences including both senior executives and senior developers with clear narratives on the technologies that my team and I routinely invent and on their application to our ecosystem partners. I thrive on new learnings and challenges and in the opportunity to be a change agent.
Domain expertise: Artificial Intelligence/Machine Learning techniques, Cyber-security, Authentication technologies including biometrics, Real-time operating systems, Networking software, Hardware & CPU architecture.
I am a versatile technology leader with a 25+ year track record of creating customer value and delivering business growth through a combination of innovation and diligent execution. My success is based on a combination of deep technical expertise, business acumen, as well as hands-on experience across advanced research, product development, product management, and ecosystem building.
I am passionate about building high achieving, cross-functional world-wide teams that create sustainable business opportunities through the application of disruptive technologies that are broadly deployed on 100s of millions of systems.
My deep technical experience & expertise starts with the creative application of Artificial Intelligence to solve cybersecurity issues, built on a deep understanding of the underlying Operating systems & Hardware environments.
I enjoy engaging audiences including both senior executives and senior developers with clear narratives on the technologies that my team and I routinely invent and on their application to our ecosystem partners. I thrive on new learnings and challenges and in the opportunity to be a change agent.
Domain expertise: Artificial Intelligence/Machine Learning techniques, Cyber-security, Authentication technologies including biometrics, Real-time operating systems, Networking software, Hardware & CPU architecture.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.